User Tools
Sidebar
Add this page to your book
Remove this page from your book
This is an old revision of the document!
Table of Contents
Security
Security is increasingly important. As PMA.core has been deployed in increasingly complex scenarios over the years, its security features have evolved, too.
Security pertaining to root-directories is situated at two levels:
- Security features that enable root-directories to access content, such as:
- Configure public/secret key combinations for S3 resources
- Configure account credentials to be used when accessing a UNC network resource path
- Prevent users from access mounted content through root directories that they are or are not allowed to do
- Define Access control lists
The following paragraphs elaborate on these respective subjects:
Accessing secured content
Based on the type of data storage that a root directory's mounting point refers to, the configuration offers different options:
Azure storage
Microsoft Azure has its own protocol, and so we provide a separate mounting point type of it.
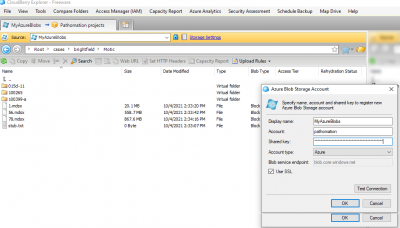
Let's say that you have an Azure container defined and put some slides in it already:
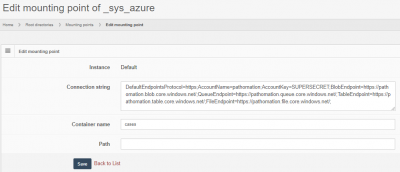
You can convert these credentials in a connectionstring:
DefaultEndpointsProtocol=https;AccountName=pathomation;AccountKey=SUPERSECRET;BlobEndpoint=https://pathomation.blob.core.windows.net/;QueueEndpoint=https://pathomation.queue.core.windows.net/;TableEndpoint=https://pathomation.table.core.windows.net/;FileEndpoint=https://pathomation.file.core.windows.net/;
This text snippet is then pasted in the connection string field of the mounting point properties:
If all goes well, you can now serve your slides from your Azure storage repositories.
Public vs private
As you have more users and more root-directories, it becomes undesirable that everybody is allowed to see everything.
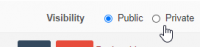
Therefore, root-directories can be marked “public” or “private”:
Public root directories are marked “public”, it means every user has access to them. They can be accessed by anybody who is a registered user in the PMA.core user repository.
Private root directories are marked “private”, it means only select users can see the content. They are only accessible by those who have been explicitly given access to be allowed to access the folder through the directory's access control list.
Access control lists
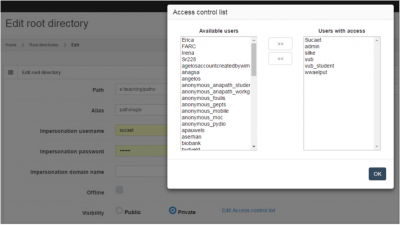
Once marked private, you can select what users are allowed to see the content of the root directory, and which ones aren't: Do this by pressing the “Edit access control list” link after you selected the “private” option:
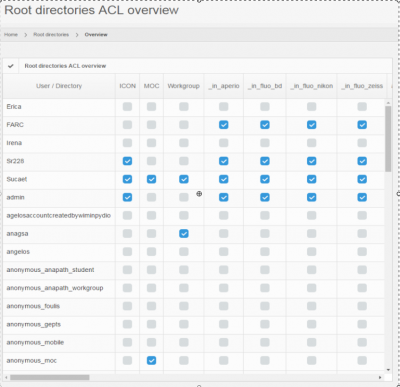
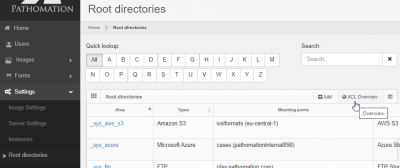
An interactive overview grid is available via the Root directories management view:
As you get even more root-directories and more users, it is useful to get an overview of who has access to what. For that, you can request the ACL report from the root-directories view.
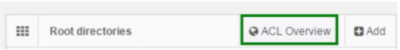
The resulting report looks like this: